Types of Personal Data that Internet Users in Western Europe Would Want Deleted After General Dat… | General data protection regulation, Data, Infographic marketing
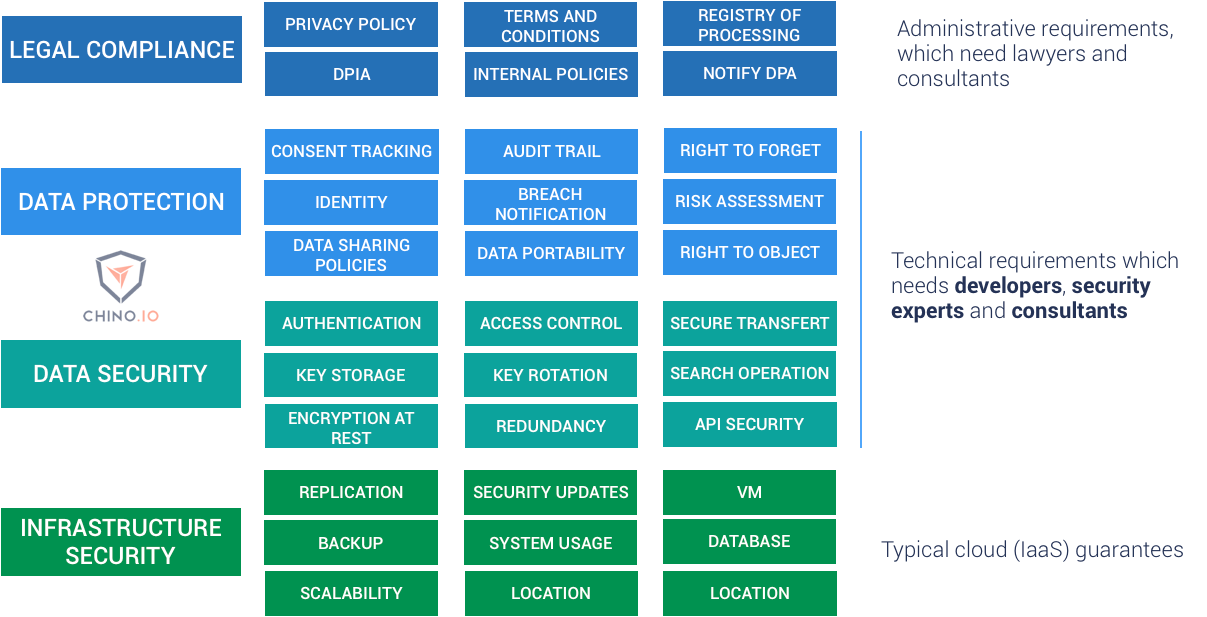
Go secure yourself: data protection and data security for digital health | by Jovan Stevovic | Towards Data Science

Data protection infographic with descriptions of types of viruses their enumeration and description vector illustration Stock Vector Image & Art - Alamy